Rustlings
In a second attempt to learn Rust well enough to actually build something of use with it, I've discovered the Rustlings tool, which is an interactive teaching tool from the Rust foundation.
Basically, you install rustlings, and it generates a series of broken rust files as a variety of exercises and quizzes for you, and then provides a CLI tool to walk you through them and track completion, etc. as well as provide hints if you are lost on how to do part of the exercise.
It's pretty slick, lets you stay all in your IDE:
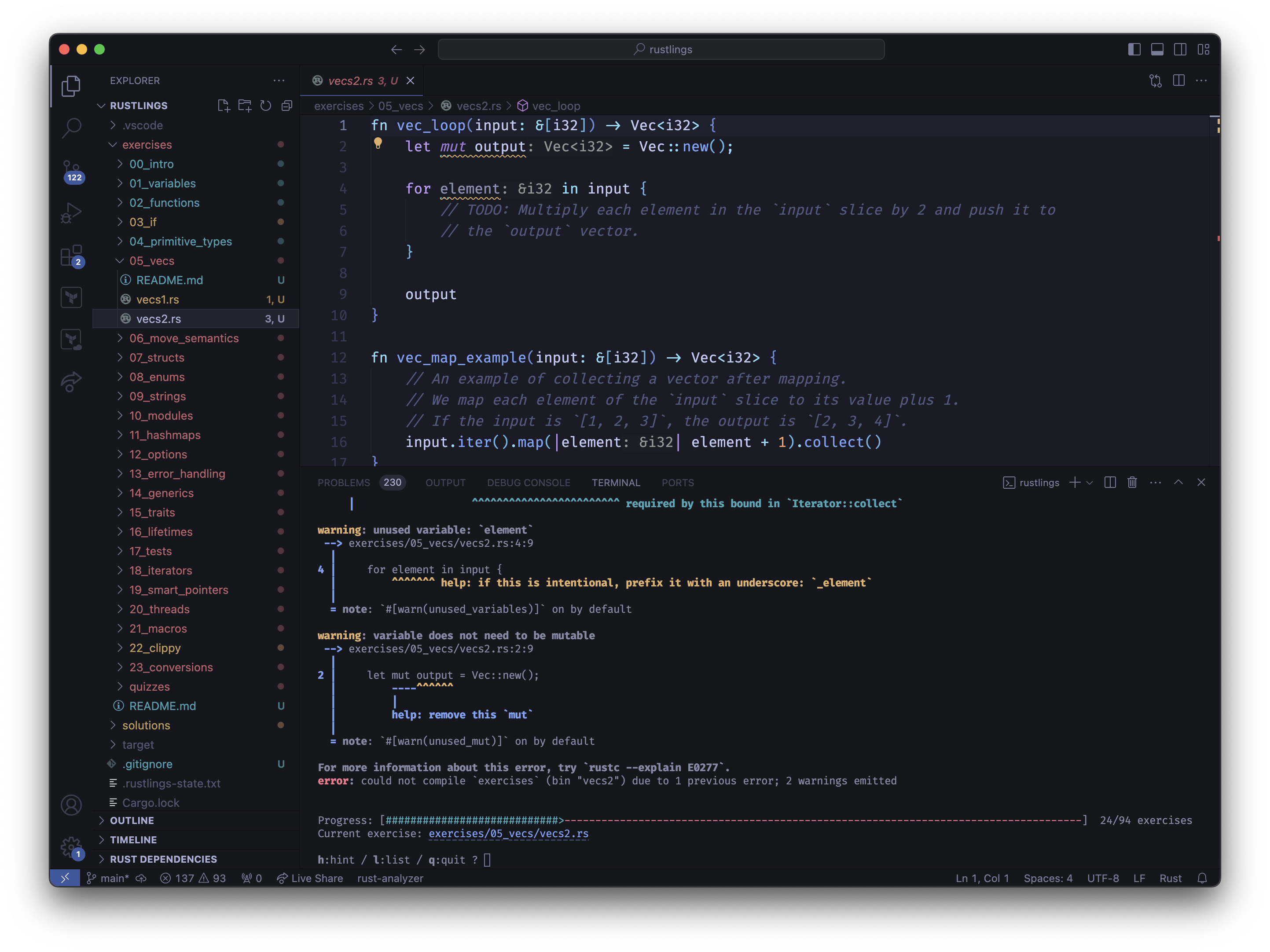
So far, it's pretty straight forward. Most slowness/awkwardness in Rust is with the slight syntactic differences from Go and Python (such as including a method return type after an arrow).
For example, the following snippet returns a Vector of i32s:
It is clear and obvious when reading it, but I'm just not used to writing it yet. The other bit that has given me pain while writing is forgetting the : symbol for type assignment (e.g. that input: &[i32] segment).
Oh, and adding ; at the end of the line....except when you don't! It's like the worst part of JavaScript :(
With that said, the compiler warnings are, as promised, insanely helpful! 'Did you mean to do X' is almost always exactly what was meant.